
Abusing Azure Active Directory at t2.fi 2019
On October 25th, I’ll be talking at t2.fi infosec conference in Helsinki. In this blog, I’ll tell what to expect in my Abusing Azure Active Directory: Who would you like to be today? presentation.

On October 25th, I’ll be talking at t2.fi infosec conference in Helsinki. In this blog, I’ll tell what to expect in my Abusing Azure Active Directory: Who would you like to be today? presentation.
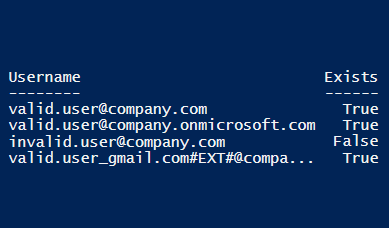
In 2017, Oliver Morton introduced a feature he found in Office 365 Active Sync, allowing enumerating the existence of the users based on http status codes. (Update: The “feature” was fixed by Microsoft on mid November 2019). In this blog, I’ll introduce my similar findings on using Microsoft API to enumerate users when Seamless SSO is enabled in Azure AD tenant.
I was honoured to hear that I was accepted to present my AADInternals toolkit at the most respected information security event in the world: Black Hat USA 2019. This is clearly one of my greatest professional achievements so far! In this blog, I’ll briefly introduce what to expect in my demo at Black Hat Arsenal.

Microsoft (finally!) announced in April 2019 the support for 8-256 character passwords in Azure AD/Office 365. This limit does not apply to users whose passwords are synced from the on-prem Active Directory (or for federated users). In this blog, I tell how to set insanely long passwords (64K+) also for cloud-only users!
On November 2018 Azure AD MFA was down over 12 hours preventing users from logging in to Office 365. Same happened in October 2019 in US data centers. As MFA is usually mandatory for administrators by company policy, they couldn’t log in either. In this blog, I’ll show how to create a backdoor to Azure AD so you can log in and bypass MFA.

By default, any user of Office 365 or Azure AD tenant can read the content of Azure AD using PowerShell and Graph API Explorer. This is a serious security issue because users have undetectable access to other users’ personal data, which violates for instance GDPR. In this blog, I’ll tell how to prevent the access.
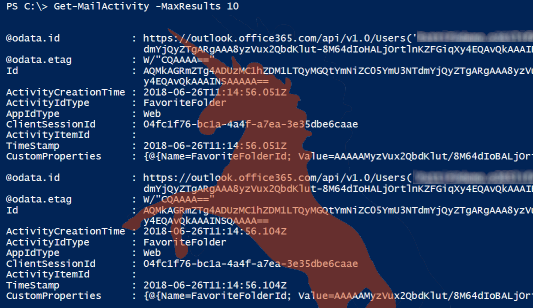
In June 2018 the existence of secret Office 365 forensics tool was confirmed. The tool refers to Microsoft’s undocumented Exchange Online Activities API. The API provides access to a granular mail activity events for up to six months old data!
To provide administrators with easy access to the API, I created a PowerShell module (EXOMailActivity). In this blog, I’ll show you how to use the module to get access to mail activity data.

It still surprises me how few know that Office 365 includes a full-fledged email encryption solution, Office Message Encryption (OME). A “new OME”, built on top of Azure Information Protection, has been available for some time now. In this blog, I’ll tell you how to setup and customise the new OME.

In short, no it’s not. In this blog, I’ll tell you three reasons why.

In this blog, I will describe a security vulnerability I discovered and reported to Microsoft in October. The vulnerability was disclosed in LIVE!360 TECHMENTOR event in Orlando on Nov 16th 2017.