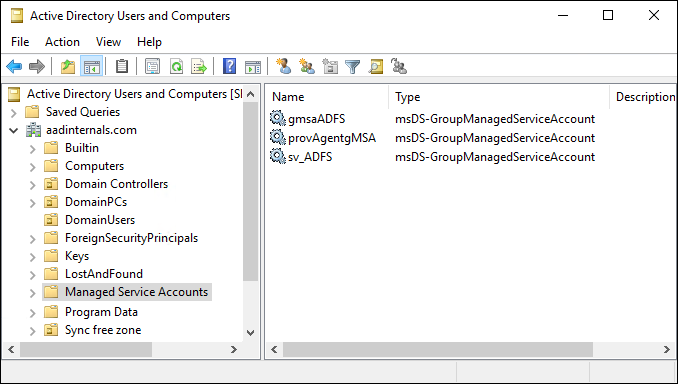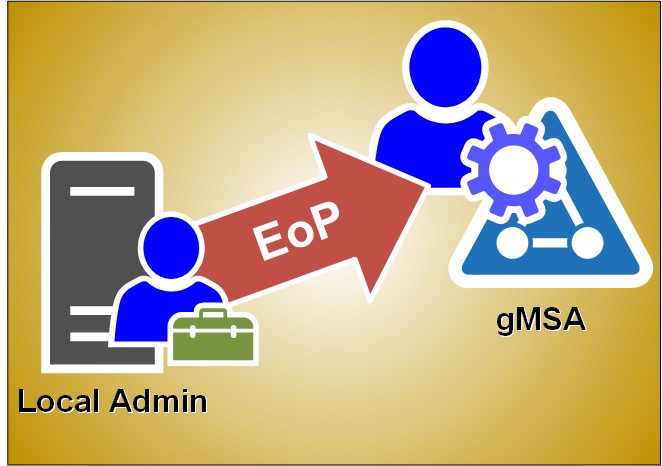
Elevation of Privilege from Local Admin to gMSA
In my previous blog post I explained how Group Managed Service Accounts (gMSA) passwords are stored locally on the servers. In this blog, I’ll share how you can easily elevate yourself from the local administrator to gMSA without a need to know the account password.
I’m already using this technique in AADInternals to execute code as AD FS service account.