
AADInternals-Endpoints 😈
In September 2024, I tweeted about my intentions to split AADInternals module in two as AVs and MDE was blocking its installation.
In this blog, I’ll explain the what and the why of the new AADInternals-Endpoints 😈 module.

In September 2024, I tweeted about my intentions to split AADInternals module in two as AVs and MDE was blocking its installation.
In this blog, I’ll explain the what and the why of the new AADInternals-Endpoints 😈 module.

Last year I gave a presentation titled Dumping NTHashes from Azure AD at TROOPERS conference.
The talk was about how the Microsoft Entra Domain Services (formerly Azure AD Domain Services) works and how it enabled dumping NTHashes from Entra ID (formerly Azure AD).
In this blog, I’ll show how Microsoft Entra Domain Services (MEDS) can be (ab)used to exfiltrate NTHashes from on-prem Active Directory.
My recent talk at the great T2 conference on DoSing Azure AD gained a lot of attention. Unfortunately, the talk was not recorded, so I decided to write a blog for those who couldn’t attend. So here we go!

A couple of weeks ago a friend of mine asked would it be possible to pre-register MFA for users in Azure AD. For short, yes it is!
In this blog, I’ll show how to pre-register OTP and SMS MFA methods using AADInternals’ Register‑AADIntMFAApp and Set‑AADIntUserMFA.
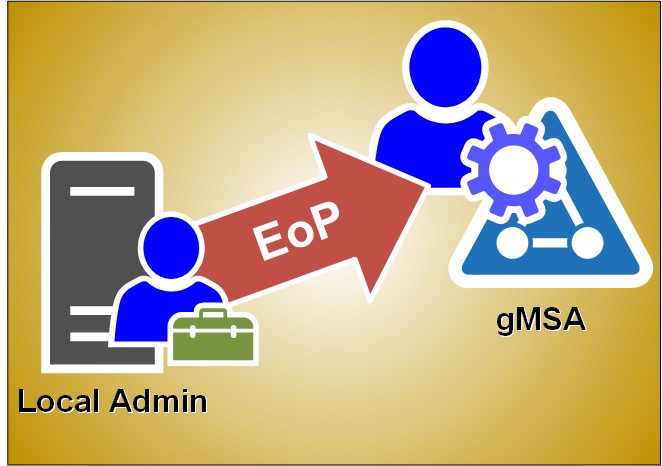
In my previous blog post I explained how Group Managed Service Accounts (gMSA) passwords are stored locally on the servers. In this blog, I’ll share how you can easily elevate yourself from the local administrator to gMSA without a need to know the account password.
I’m already using this technique in AADInternals to execute code as AD FS service account.
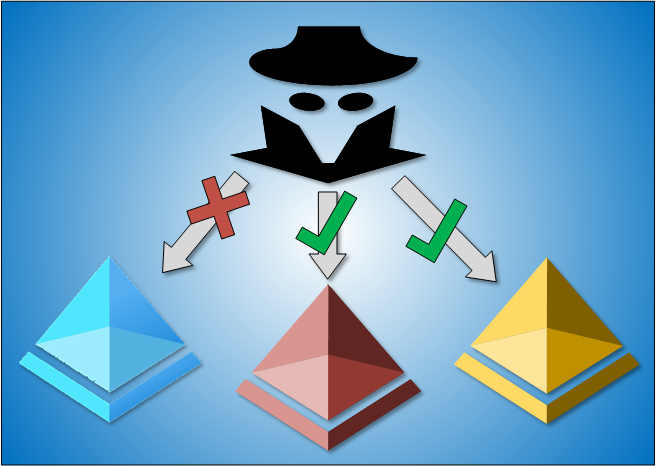
Multi-factor Authentication (MFA) and Conditional Access (CA) policies are powerful tools to protect Azure AD users’ identities.
For instance, one may allow access only from compliant devices and require MFA from all users.
However, because of Azure AD authentication platform architecture, users can bypass home tenant MFA and CA policies when logging in directly to resource tenants.
This blog post tries to shed some light on how Azure AD authentication works under-the-hood. We’ll introduce the issue, describe how to exploit it, show how to detect exploitation, and finally, how to prevent the exploitation.
The blog is co-authored with @SravanAkkaram and is based on his findings.
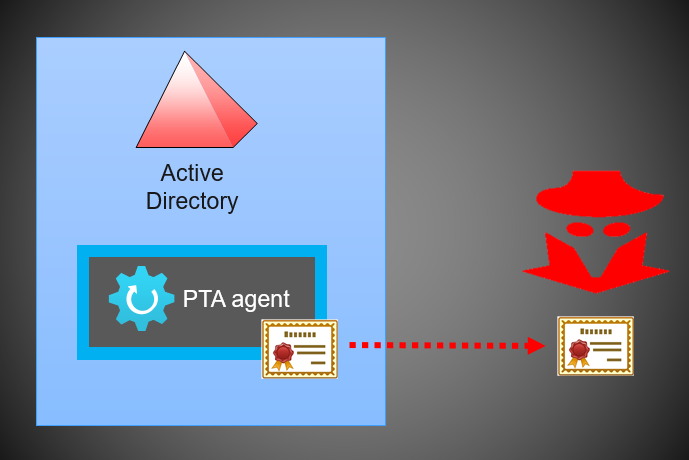
In 13 September 2022, Secureworks published a Threat Analysis: Azure Active Directory Pass-Through Authentication Flaws.
The vulnerabilities discovered by our team allows threat actors to gain persistent and undetected access to the target Azure AD tenant.
In this blog post, I’ll show how the attack can be conducted using AADInternals and standalone Windows server.
Group Managed Service Accounts (gMSA’s) can be used to run Windows services over multiple servers within the Windows domain.
Since the launch of Windows Server 2012 R2, gMSA has been the recommended service account option for AD FS.
As abusing AD FS is one of my favourite hobbies, I wanted to learn how gMSAs work.

In August 2022, I’ll have several presentations regarding Azure AD security, open-source tools, and bug bounties.
I’ll be presenting at TECHMENTOR, Black Hat Arsenal, DEF CON demo labs, and Cloud Village.
If you like to have a chat on anything Azure AD related, want to say hi or get AADInternals sticker, check my schedule!
In my previous blog posts I’ve covered details on PRTs, BPRTs, device compliance, and Azure AD device join.
In this blog, I’ll show how to steal identities of existing Azure AD joined devices, and how to fake identies of non-AAD joined Windows devices with AADInternals v0.6.6.

In 2018, I blogged first time about risks related to Delegated Administrative Privileges (DAP) given to Microsoft partners. Now, in 2021, Microsoft blogged how NOBELIUM exploited DAP to compromise customers of some Microsoft partners.
In this blog, I’ll explain why DAP is so dangerous, how to exploit it, how to detect exploitation, and how to view partner related information with AADInternals v0.6.5.
AADInternals toolkit is best known of its offensive or red teams tools. Its origins, however, is in administration - especially for tasks not supported by official tools.
In this blog, I’ll introduce recent additions to the admin & blue team tools and also some old goodies!
Azure AD Connect Health is a feature that allows viewing the health of on-prem hybrid infrastructure components, including Azure AD Connect and AD FS servers. Health information is gathered by agents installed on each on-prem hybrid server. Since March 2021, also AD FS sign-in events are gathered and sent to Azure AD.
In this write-up (based on a Threat Analysis report by Secureworks), I’ll explain how anyone with a local administrator access to AD FS server (or proxy), can create arbitrary sign-ins events to Azure AD sign-ins log. Moreover, I’ll show how Global Administrators can register fake agents to Azure AD - even for tenants not using AD FS at all.

I’ve talked about AD FS issues for a couple years now, and finally, after the Solorigate/Sunburst, the world is finally listening 😉
In this blog, I’ll explain the currently known TTPs to exploit AD FS certificates, and introduce a totally new technique to export the configuration data remotely.

Devices (endpoints) are a crucial part of Microsoft’s Zero Trust concept. Devices can be Registered, Joined, or Hybrid Joined to Azure AD. Conditional Access uses the device information as one of the decisions criteria to allow or block access to services.
In this blog, I’ll explain what these different registration types are, what happens under-the-hood during the registration, and how to register devices with AADInternals v0.4.6.

In October 2020, someone contacted me and asked whether it would be possible to create BPRTs using AADInternals. I hadn’t even heard of BPRTs, but was eventually able to help him to create BPRTs. Now this functionality is included in AADInternals v0.4.5.
In this blog, I’ll explain what BPRTs are and how they can be used to join multiple devices to both Azure AD and Intune. I’ll also show the dark side of BPRTs: how they can be used to conduct DOS attacks against Azure AD, and how to detect and prevent this.

Administrators can use teams policies for controlling what users can do in Microsoft Teams.
In this blog, I’ll show that these policies are applied only in client and thus can be easily bypassed.
The new AADInternals release v0.4.4 AADInternals Cloud Identity Summit 2020 edition is now released! Read on to see the list of updates and new features.

The ongoing global phishing campaings againts Microsoft 365 have used various phishing techniques. Currently attackers are utilising forged login sites and OAuth app consents.
In this blog, I’ll introduce a new phishing technique based on Azure AD device code authentication flow. I’ll also provide instructions on how to detect usage of compromised credentials and what to do to prevent phishing using the new technique.
Azure Cloud Shell is a browser-based shell for managing Azure resources using your favourite shell, Bash or PowerShell. Cloud Shell is typically used from Azure Portal. It provides an easy access to Azure CLI, Azure PowerShell and Azure AD PowerShell.
In this blog, I’ll introduce a new way to access Cloud Shell from PowerShell (requires AADInternals v0.4.3 or newer).