Unnoticed sidekick: Getting access to cloud as an on-prem admin
This post is part 5⁄5 of Azure AD and Microsoft 365 kill chain blog series.
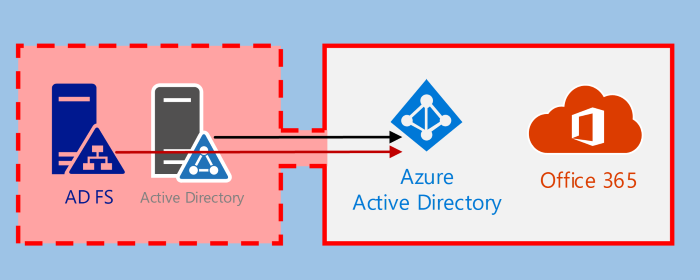
Although on-prem administrators doesn’t usually have admin rights to Azure AD, they can have access to crucial information, such as Azure AD Connect, ADFS, and Active Directory. Administrators of these services can easily get admin rights to Azure AD to manipulate and impersonate users.
In this blog, using AADInternals v0.4.0, I’ll show how to get Global Admin access and how to impersonate users as an on-prem administrator.